This how-to is a practical follow-up to the previous article where I talked about the importance of using HTTPS. In this how-to I want to show you how to configure Apache HTTP Server (which obviously also supports HTTPS) to get a web server that provides a Shiny Server, an RStudio Server, and if you want also an API end-point with Plumber; all provided via HTTPS.
The goal
The objectives of this project are essentially two:
- obtain a single web address to access both Shiny applications and RStudio server (with authentication)
- protect communication with an SSL (HTTPS) encryption layer.
With Apache Web Server you will be able also:
- to integrate other pages or web applications into the website in the same way, having a dedicated address for each one.
- to integrate different Shiny servers, for different uses and users
Example: RStudio via HTTPS
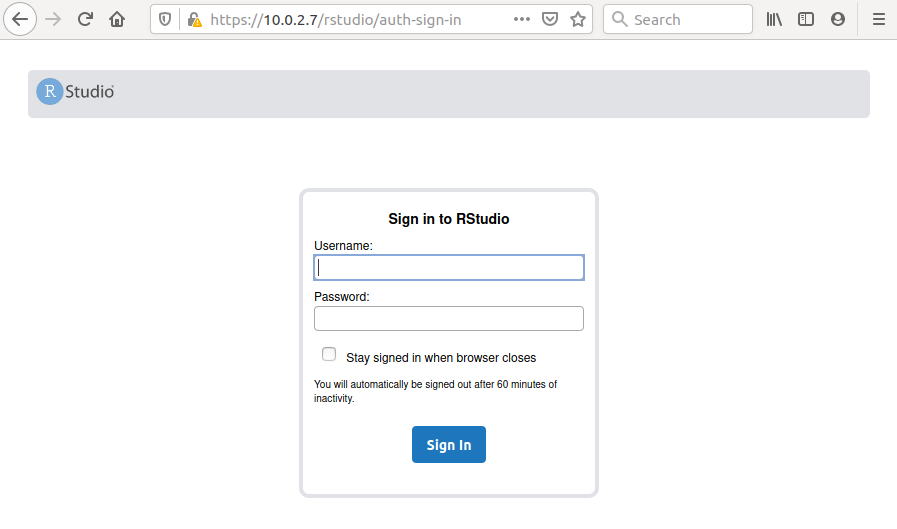
Relation to Professional versions
The content of this how-to is applied to the free versions, but does not replace Shiny Server Pro and Rstudio Server Pro, which together with HTTPS provide other features: a more sophisticated authentication system, multithreading server, control panel for administrators and more. However, the presented method can still be useful for bundling applications into a single web access point.
What is Apache HTTP Server?
“Apache HTTP Server, or more commonly Apache is the name of a free web server developed by the Apache Software Foundation. It is the most popular modular web server platform, capable of running on a large variety of operating systems, including UNIX / Linux, Microsoft Windows and OpenVMS. It is a software that performs the functions of information transport, internetwork and connection, and has the advantage of offering control functions for security such as those performed by a proxy." IT-Wikipedia
We are therefore talking about quality software, widely tested, Open Source (Apache license), and therefore suitable for production environments.
How-To
System used and Prerequisites
These instructions assume that these two servers are up and running:
- RStudio-Server at URL http://localhost:8787
- Shiny-Server at URL http://localhost:3838
The following configuration is done for both servers, but everything is feasible even with only one of the two provided, you only need to fix the Apache configuration file that we will see later.
The system used to test the instructions in this guide is Ubuntu 20.04, but Apache is available for all major Linux distributions and the configuration is the same, just change the name of the installed packages.
Installing the Apache HTTP Server
Apache can be installed from any package manager. Here I show how to install it from Bash, as if you want to install it on a server it may be useful to connect with SSH to have a remote BASH. Along with apache2 install other packages and enable some Apache modules which will come in handy later:
| |
Note: in older versions of ubuntu you may not find apache2-bin and need libapache2-mod-proxy-html instead.
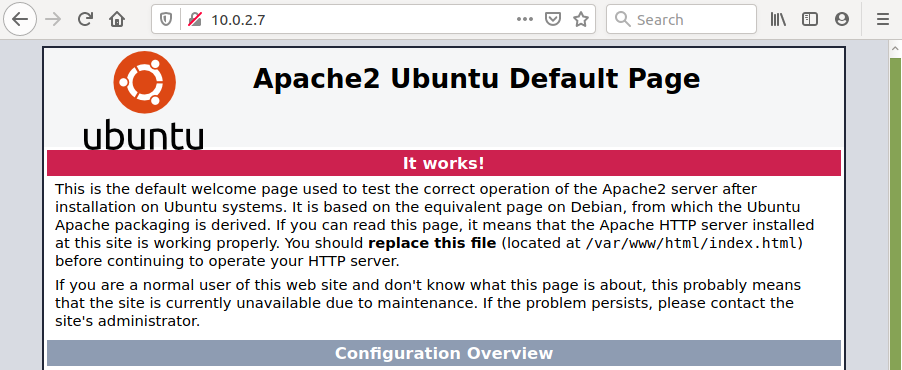
At this point you should be able to access the default apache page from your browser: http://localhost (or via ip http://10.0.2.7, if you are accessing from another server) . Note: we are using http://, in fact Firefox indicates that the connection is not protected with a padlock crossed out in red.
Enable HTTPS
First of all, certificates are needed. By doing this how-to without a domain it is convenient to generate self-signed ones. We then generate the two files /etc/ssl/private/selfsigned.key and/etc/ssl/certs/selfsigned.crt with openssl from BASH, as root user with the command:
| |
Now, you need to configure Apache to make HTTPS connection available. To do this create the /etc/apache2/sites-available/r-ssl.conf:
| |
Now, enable the apache ssl module, enable the virtual host and reload the configuration:
| |
Now open the browser at the URL https://localhost/ (or using the ip: https://10.0.2.7). Note: When using a self-signed certificate, you receive this message:
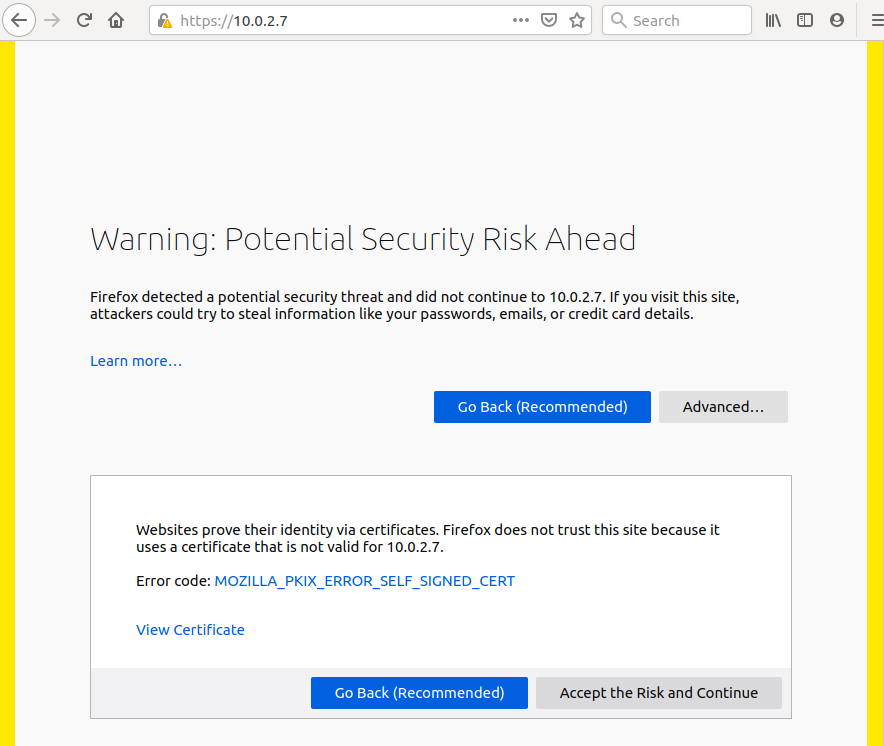
Note that there is no risk now, the message warns of the possibility that an attacker could exploit the lack of server authentication for malicious purposes. The problem is adequately resolved with a certificate signed by a certification authority (Certification Authority CA), whose generation process is not the scope of this article. What is explained in this article remains valid with signed certificates: just replace the .key and .crt files to use HTTPS to its full potential.
For now, click on Advanced and then on Accept the Risk and Continue to fix the problem.
The browser should display the following default page:
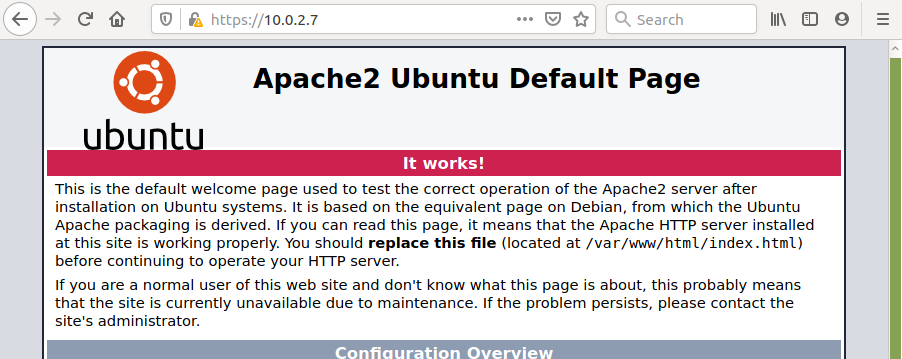
HTTPS is now active.
Note: The yellow triangle means the certificate is unsigned. The page is by default and can be replaced, for example, with a Home-Page that displays the links to the Shiny page and to the RStudio Server page.
Shiny Https
As defined in the configuration file, the address to access Shiny is https://localhost/shiny (or using the ip: https://10.0.2.7/shiny) :
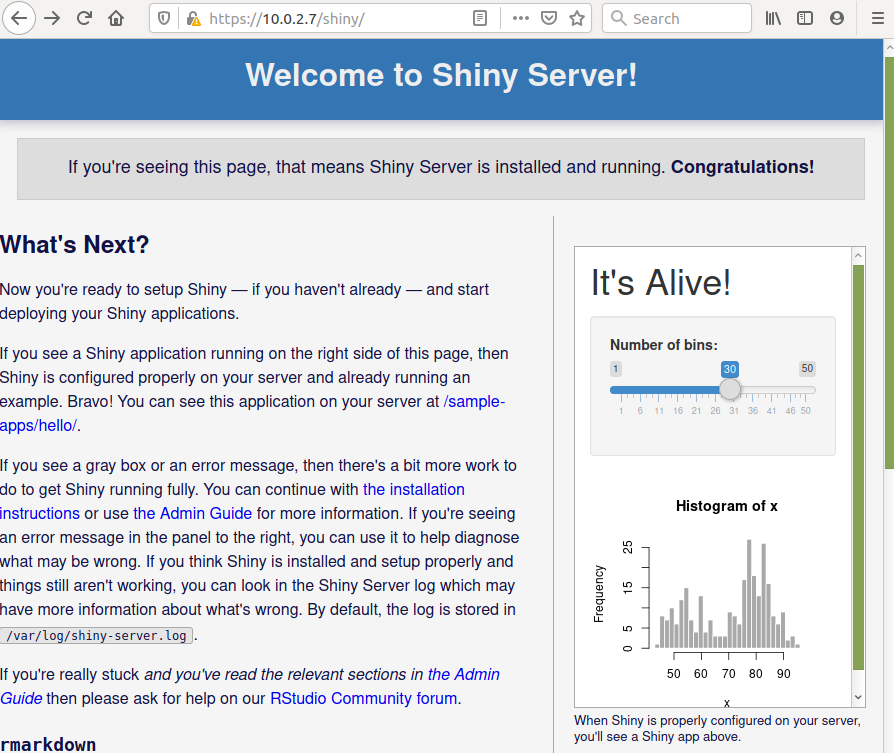
Note that instead of the usual http://10.0.2.7:3838, you are using HTTPS and its default port (not 3838, but 443, which is omitted because it is a default). The communication with the Shiny server is passing through the HTTPS connection thanks to the Apache server.
Now let’s see how to do the same step on RStudio Server and then we’ll see how to disable access to http://10.0.2.7:3838 which is now obsolete.
RStudio Server Https
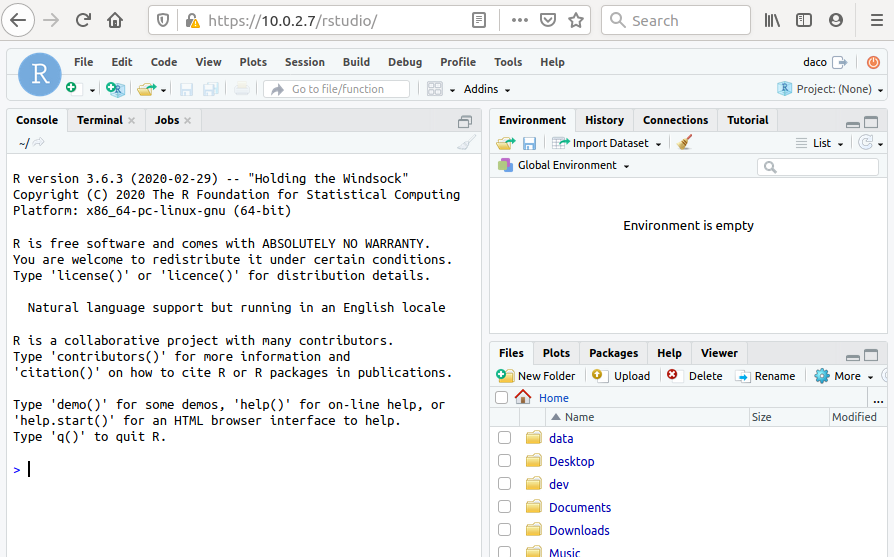
In a very similar way, the address to access RStudio Server is https://localhost/rstudio (or using the IP: https://10.0.2.7/rstudio):

from here you can log in and use R:
Plumber API Https
In order to get Plumber API or any web server you want in https, you can use the same method. Assuming you have Plumber listening on port 8000, add the configuration to the r-ssl.conf above:
| |
Improve Security
Now that you can access and use Shiny and RStudio through a secure connection, in order to make a more robust system, you must prevent the user from using the non-secure connection. Therefore you need to:
- disable direct access to application servers:
http://10.0.2.7:3838andhttp://10.0.2.7:8787 - redirect the user accessing via http (
http://10.0.2.7/...) to use HTTPS
RStudio Server
Add a line to the file /etc/rstudio/rserver.conf to instruct RStudio Server to listen to connections from localhost only.
| |
Restart the server:
| |
The result is that the server now ignores connections from another address. (Note that http://localhost:8787 will continue to work).
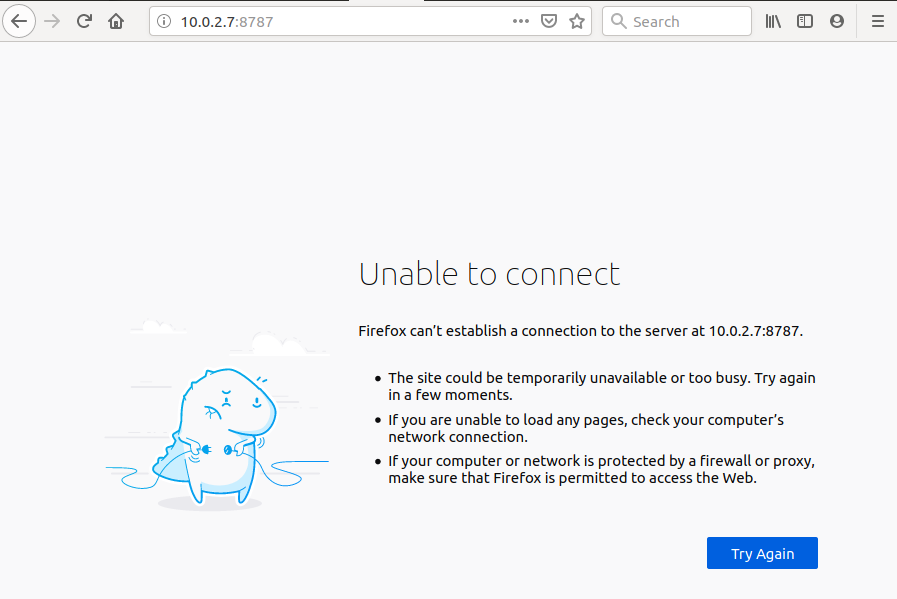
Shiny Server
In the /etc/shiny-server/shiny-server.conf file change the line
| |
indicating to respond to connections in the local network:
| |
Reload the new configuration:
| |
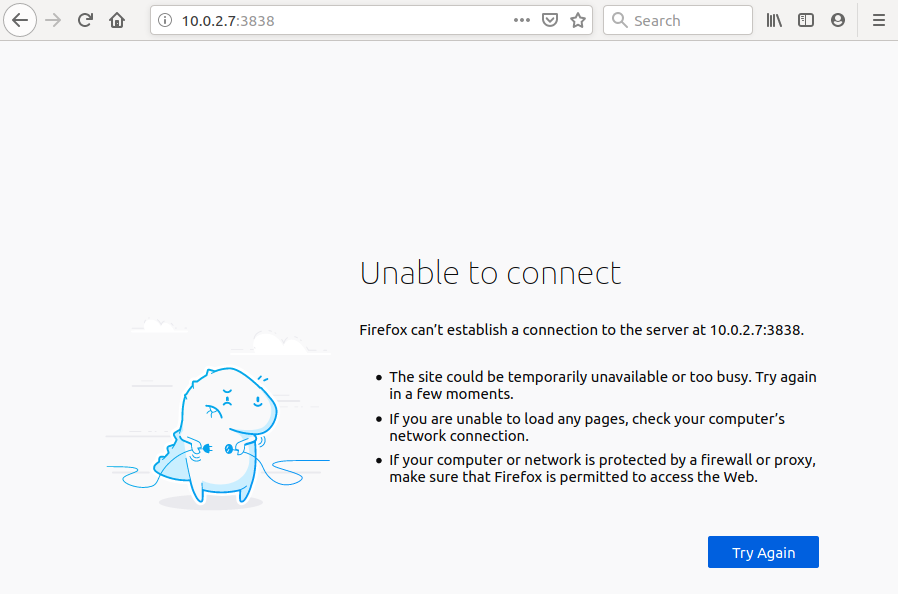
HTTPS Mandatory
In /etc/apache2/sites-available/000-default.conf before closing the </VirtualHost> tag add the instructions for the redirect:
| |
And reload the configuration:
| |
Now, every time the user requests a page via http://... it is redirected to the same route in https://...
Firewall
It is advisable to activate a firewall that blocks all incoming connections except those on ports 80 (HTTP: used to make redirect to https possible) and 443 (HTTPS port) where all traffic relating to Apache, Shiny Server and RStudio Server will pass. Note that the firewall provides an additional layer of security by blocking direct access to ports 3838 and 8787.
Conclusions
With this simple configuration you have collected various web services in a single access point and made them usable exclusively through a secure protocol. Furthermore this configuration is completely transparent to the Shiny and RStudio servers which are configured independently from Apache.
Of course this is just a start, and among the applicable improvements I would mention:
Strengthen security by configuring a firewall.
Create and use a domain associated with a certificate signed by a CA.
Use a single authentication system for the various services (now protected by HTTPS).
If you need to use RStudio server, you need to structure the server with adequate users, credentials, permissions on the filesystem in order to facilitate team collaboration.
Comments
Comment on Linkedin
Comment on Twitter